Universal Cloud Storage by LinkDaddy: Service and Press Release Insights
Wiki Article
How Universal Cloud Storage Solutions Can Boost Data Protection and Conformity
In the realm of data security and compliance, the advancement of global cloud storage services has presented an engaging remedy to attend to journalism concerns faced by companies today. With a range of innovative functions such as improved information encryption, automated conformity surveillance, secure data access controls, catastrophe healing solutions, and governing conformity automation, the duty of cloud storage solutions in fortifying information defense and adherence to industry regulations can not be underrated. Nonetheless, the complexities of just how these services flawlessly integrate into existing procedures and systems to boost security requirements and compliance methods might just offer a fresh viewpoint on the intersection of modern technology and data administration.Enhanced Data File Encryption
Enhancing data security strengthens the safety and security actions of cloud storage services, guaranteeing durable security for sensitive information - Universal Cloud Storage Service. By carrying out advanced encryption algorithms, cloud service suppliers can dramatically decrease the risk of unauthorized access to saved information.Moreover, enhanced information encryption plays an important role in regulative conformity, especially in sectors with strict information security requirements such as medical care and finance. In conclusion, focusing on boosted data encryption is essential for strengthening the security stance of cloud storage space services and keeping information discretion.
Automated Conformity Monitoring
The application of enhanced information security within cloud storage services not only fortifies data safety and security however likewise sets the structure for automated conformity surveillance mechanisms. Automated conformity surveillance plays a vital function in making certain that organizations abide by industry regulations and inner plans concerning information handling and storage. By integrating automated conformity tracking devices right into cloud storage services, companies can streamline the procedure of tracking and enforcing compliance requirements. These devices can automatically check information kept in the cloud, determine sensitive details, and make certain that it is handled in accordance with relevant policies. Additionally, automated conformity tracking can create real-time records and alerts to inform stakeholders of any kind of non-compliance problems, permitting punctual remediation actions. Generally, the assimilation of automated compliance monitoring within global cloud storage space solutions improves information safety and security by giving organizations with an aggressive approach to preserving conformity and mitigating risks related to information violations and regulatory penalties.Secure Data Gain Access To Controls
Exactly how can companies properly manage and impose safe information gain access to regulates within cloud storage space solutions? Protected data access controls are essential for preserving the confidentiality and honesty of sensitive info kept in the cloud.Furthermore, companies can use security techniques to safeguard information both en route and at rest within the cloud storage space environment. Role-based my website access control (RBAC) can assist improve gain access to management by appointing consents based upon predefined roles, streamlining the procedure of revoking and providing accessibility rights. Regular audits and monitoring of access logs are vital for identifying any kind of unusual tasks and guaranteeing conformity with protection plans. By integrating these techniques, organizations can boost information protection and minimize the risks related to unapproved accessibility in cloud storage space services.
Calamity Recuperation Solutions
In the world of cloud try this site storage space services, durable calamity recuperation remedies play an essential role in securing data integrity and connection despite unanticipated disturbances. These solutions are crucial for organizations to alleviate the effect of calamities such as equipment failures, cyber-attacks, or natural tragedies that might possibly result in information loss or downtime.
Executing an extensive catastrophe healing strategy includes creating backups of important information and applications, establishing repetitive systems for failover abilities, and defining clear treatments for recovering operations swiftly. Cloud storage space services offer advantages in disaster healing by supplying scalable storage alternatives, automatic back-ups, and geographically varied information facilities that boost redundancy and durability.

Regulatory Conformity Automation
In the middle of the critical world of disaster recuperation services within cloud storage space solutions, the assimilation of regulatory conformity automation becomes a critical mechanism for making certain adherence to industry standards and legal demands. Regulatory conformity automation involves using technology to simplify and streamline the process of conference governing obligations, such as information security laws like GDPR or industry-specific standards like HIPAA in healthcare. By automating tasks such as information security, gain access to controls, and audit routes, companies can substantially reduce the threat of non-compliance and the associated charges.
Final Thought
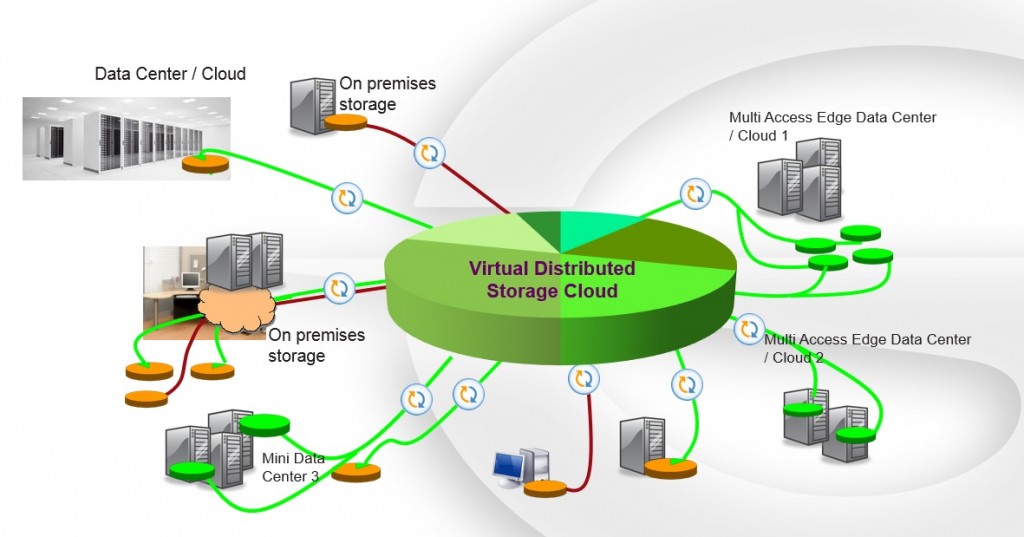
With a range of advanced attributes such as improved data security, automated compliance monitoring, safe and secure data gain access to controls, calamity recuperation services, and regulative compliance automation, the function of cloud storage solutions in fortifying data defense and published here adherence to market regulations can not be downplayed.The application of boosted information file encryption within cloud storage space solutions not just fortifies information security however additionally sets the foundation for automated conformity monitoring mechanisms. On the whole, the combination of automated conformity monitoring within global cloud storage space solutions boosts information security by providing companies with a positive method to maintaining conformity and mitigating threats linked with data violations and regulative fines.
In conclusion, global cloud storage space solutions supply boosted information security, automated compliance monitoring, secure data accessibility controls, catastrophe healing options, and regulatory conformity automation. By utilizing these solutions, services can reduce dangers associated with information violations, ensure regulative compliance, and enhance overall information defense measures.
Report this wiki page